知识库与软件
FR2000-M濠电姷鏁告慨鐑藉极閸涘﹥鍙忛柣鎴f閺嬩線鏌涘☉姗堟敾闁告瑥绻橀弻锝夊箣閿濆棭妫勯梺鍝勵儎缁舵岸寮诲☉妯锋婵鐗婇弫楣冩⒑閸涘﹦鎳冪紒缁橈耿瀵鏁愭径濠勵吅闂佹寧绻傚Λ顓炍涢崟顖涒拺闁告繂瀚烽崕搴g磼閼搁潧鍝虹
文档编号:473
浏览:17078 评分:38
最后更新于:2009-09-07
用户网络环境:
某公司总部使用的H3C SecPath F100-E:内网地址192.168.16.1/22,公司分部HiPER:内网地址192.168.0.1/24,现在需要实现两边通过建立IPSEC隧道实现互相通信。
H3C的配置:
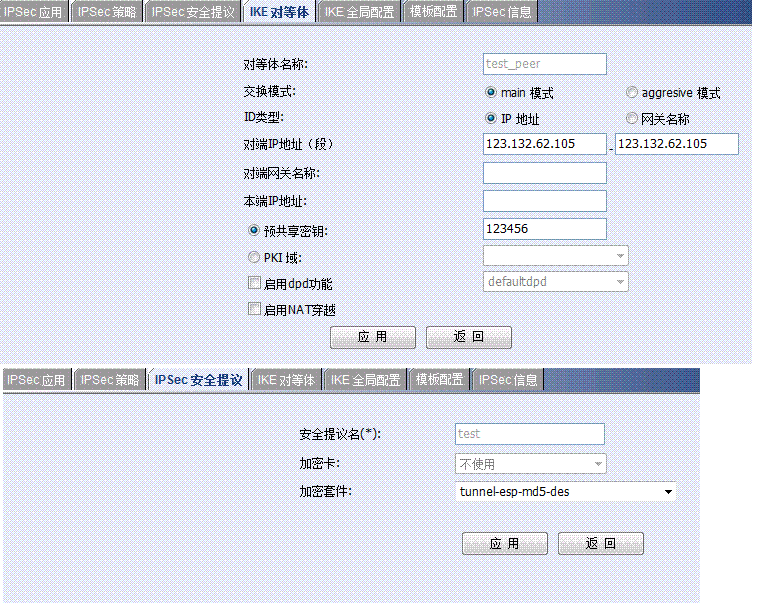
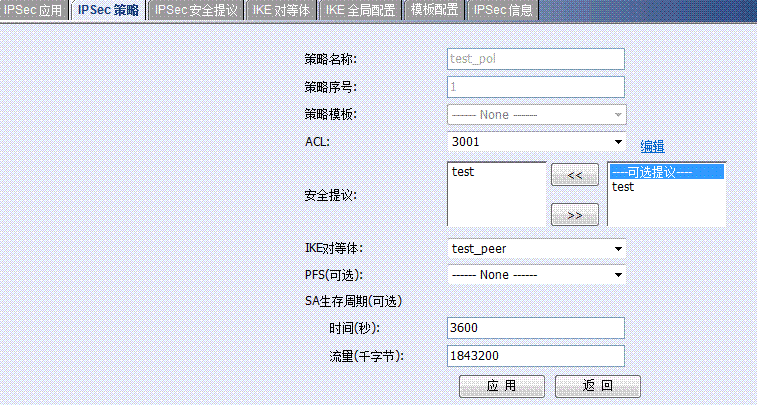
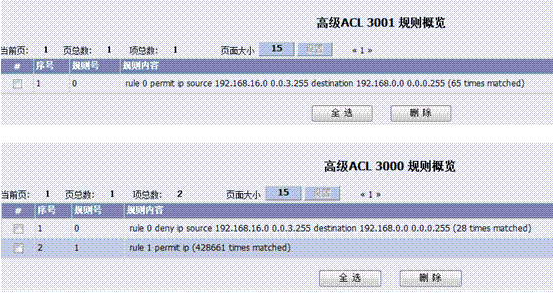
特别要注意这条3000的ACL,序号为1的ACL意思是禁止192.168.16.0/22的地址访问192.168.0.0/24的时候走NAT。这条必不可少。
H3C命令行的配置:
<H3C>disp saved-configuration
#
sysname H3C
#
l2tp enable
#
firewall packet-filter enable
firewall packet-filter default permit
#
firewall statistic system enable
#
DNS server 202.102.152.3
DNS server 202.102.128.68
#
radius scheme system
server-type extended
#
domain system
ip pool 1 192.168.1.2 192.168.1.253
#
ike proposal 1
dh group2
authentication-algorithm md5
#
ike dpd defaultdpd
#
ike peer test_peer
pre-shared-key 123456
remote-address 123.132.62.105
#
ipsec proposal test
#
ipsec policy test_pol 1 isakmp
security acl 3001
ike-peer test_peer
proposal test
#
acl number 3000
rule 0 deny ip source 192.168.16.0 0.0.3.255 destination 192.168.0.0 0.0.0.255
rule 1 permit ip
acl number 3001
rule 0 permit ip source 192.168.16.0 0.0.3.255 destination 192.168.0.0 0.0.0.255
acl number 3002
rule 0 permit ip source 192.168.16.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
acl number 3003
rule 0 permit ip source 192.168.16.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
acl number 3004
rule 0 permit ip source 192.168.16.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
acl number 3333
rule 1 deny tcp destination-port eq 135
rule 2 deny udp destination-port eq 135
rule 3 deny udp destination-port eq netbios-ns
rule 4 deny udp destination-port eq netbios-dgm
rule 5 deny tcp destination-port eq 139
rule 6 deny udp destination-port eq netbios-ssn
rule 7 deny tcp destination-port eq 445
rule 8 deny udp destination-port eq 445
rule 9 deny tcp destination-port eq 539
rule 10 deny udp destination-port eq 539
rule 11 deny udp destination-port eq 593
rule 12 deny tcp destination-port eq 593
rule 13 deny udp destination-port eq 1434
rule 14 deny udp destination-port eq 1433
rule 15 deny tcp destination-port eq 4444
rule 16 deny tcp destination-port eq 9996
rule 17 deny tcp destination-port eq 5554
rule 18 deny udp destination-port eq 9996
rule 19 deny udp destination-port eq 5554
rule 20 deny tcp destination-port eq 137
rule 21 deny tcp destination-port eq 138
rule 22 deny tcp destination-port eq 1025
rule 23 deny udp destination-port eq 1025
rule 24 deny tcp destination-port eq 9995
rule 25 deny udp destination-port eq 9995
rule 26 deny tcp destination-port eq 1068
rule 27 deny udp destination-port eq 1068
rule 28 deny tcp destination-port eq 1023
rule 29 deny udp destination-port eq 1023
#
interface Virtual-Template0
ppp authentication-mode pap
ip address 192.168.1.1 255.255.255.0
remote address pool 1
#
interface Aux0
async mode flow
#
interface Ethernet0/0
description CNC_OUT
ip address x.x.x.x 255.255.255.248
firewall packet-filter 3333 inbound
nat outbound 3000
nat server protocol tcp global 221.1.217.154 5475 inside 192.168.16.12 5475
nat server protocol tcp global 221.1.217.154 5476 inside 192.168.16.12 5476
nat server protocol tcp global 221.1.217.154 5477 inside 192.168.16.12 5477
nat server protocol tcp global 221.1.217.154 5478 inside 192.168.16.12 5478
nat server protocol tcp global 221.1.217.154 82 inside 192.168.16.12 82
ipsec policy test_pol
#
interface Ethernet0/1
#
interface Ethernet0/2
description INTERNAL
ip address 192.168.16.1 255.255.255.0
#
interface Ethernet0/3
description SERVER
ip address 192.168.17.101 255.255.255.252
#
interface Encrypt2/0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
add interface Ethernet0/1
add interface Ethernet0/2
set priority 85
#
firewall zone untrust
add interface Ethernet0/0
add interface Virtual-Template0
set priority 5
#
firewall zone DMZ
add interface Ethernet0/3
set priority 50
#
firewall interzone local trust
#
firewall interzone local untrust
#
firewall interzone local DMZ
#
firewall interzone trust untrust
#
firewall interzone trust DMZ
#
firewall interzone DMZ untrust
#
l2tp-group 1
undo tunnel authentication
mandatory-lcp
allow l2tp virtual-template 0
#
ip route-static 0.0.0.0 0.0.0.0 221.1.217.153 preference 60
ip route-static 192.168.10.0 255.255.255.0 192.168.16.254 preference 60
ip route-static 192.168.11.0 255.255.255.0 192.168.16.254 preference 60
#
firewall defend ip-spoofing
firewall defend land
firewall defend smurf
firewall defend fraggle
firewall defend winnuke
firewall defend icmp-redirect
firewall defend icmp-unreachable
firewall defend source-route
firewall defend route-record
firewall defend tracert
firewall defend ping-of-death
firewall defend tcp-flag
firewall defend ip-fragment
firewall defend large-icmp
firewall defend teardrop
firewall defend ip-sweep
firewall defend port-scan
firewall defend arp-spoofing
firewall defend arp-flood
firewall defend frag-flood
firewall defend syn-flood enable
firewall defend udp-flood enable
firewall defend icmp-flood enable
#
user-interface con 0
user-interface aux 0
user-interface vty 0 4
authentication-mode scheme
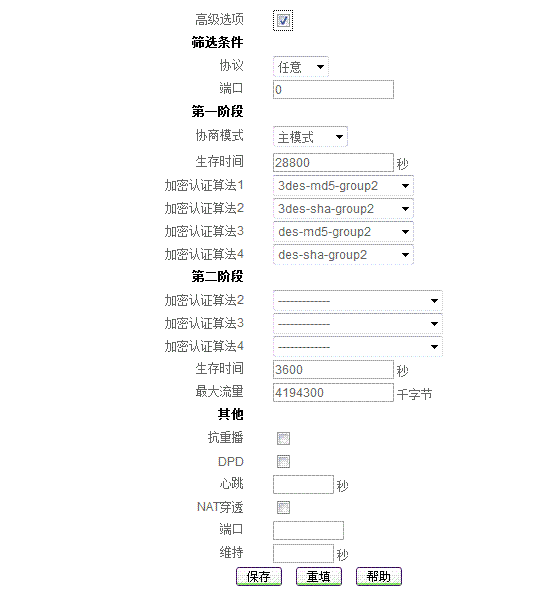
艾泰科技的配置:


























 沪公网安备 31011702003579号
沪公网安备 31011702003579号