知识库与软件
-1' OR 374=374 or 'mF5u9TGo'='
文档编号:38
浏览:8857 评分:14
最后更新于:2008-08-19
在HiPER路由器上屏蔽“冲击波”、“震荡波”病毒
1、“冲击波”病毒感染个人电脑之后,电脑出现如下症状:
1)莫名其妙地死机或重新启动计算机;
2)IE浏览器不能正常地打开链接;
3)不能复制粘贴;
4)有时出现应用程序,比如Word异常;
5)网络变慢;
6)最重要的是,在任务管理器里有一个叫“msblast.exe”的进程在运行。
关键是感染了病毒的个人电脑会随机向外发送大量的ICMP包以及向目的端口为135/137/139/445/1025/5554/9996的端口发送大量的广播包,造成路由器端口拥塞,直至用户整个内部网络/外部网络的瘫痪。
使用show ip nat translation命令查找感染冲击波病毒的个人电脑。
hiper% show ip nat translation
list all translations
Id srcAddress sPort P destAddress dPort outP inP globalIp
1 192.168.100.221 4082 T 218.7.38.2 445 812 7 61.171.208.145
2 192.168.100.221 4083 T 202.96.209.5 445 346 1 61.171.208.145
3 192.168.100.221 4084 T 218.7.38.2 445 532 7 61.171.208.145
4 192.168.100.221 1191 I 65.54.249.126 0 60 51 61.171.208.145
… …
可以看出192.168.100.221在向外大量的发送ICMP包以及向目标端口445大量发送数据包,可以判断实感染了“冲击波”病毒。
1 192.168.100.221 4082 T 218.7.38.2 445 812 7 61.171.208.145
2 192.168.100.221 4083 T 202.96.209.5 445 346 1 61.171.208.145
3 192.168.100.221 4084 T 218.7.38.2 445 532 7 61.171.208.145
4 192.168.100.221 1191 I 65.54.249.126 0 60 51 61.171.208.145
… …
可以看出192.168.100.221在向外大量的发送ICMP包以及向目标端口445大量发送数据包,可以判断实感染了“冲击波”病毒。
2、“震荡波”病毒感染个人电脑后,电脑出现如下症状:
1)莫名其妙地死机或重新启动计算机;
2)任务管理器里有一个叫“avserve.exe”、“avserve2.exe”或者“skynetave.exe”的进程在运行;
3)在系统目录下,产生一个名为avserve.exe、avserve2.exe、skynetave.exe的病毒文件;
4)系统速度极慢,CPU占用100%。
关键是感染了病毒的个人电脑会随机向外发送大量的ICMP包以及向目的端口为135/137/139/445/1025/5554/9996的端口发送大量的广播包,造成路由器端口拥塞,直至用户整个内部网络/外部网络的瘫痪。
1)莫名其妙地死机或重新启动计算机;
2)任务管理器里有一个叫“avserve.exe”、“avserve2.exe”或者“skynetave.exe”的进程在运行;
3)在系统目录下,产生一个名为avserve.exe、avserve2.exe、skynetave.exe的病毒文件;
4)系统速度极慢,CPU占用100%。
关键是感染了病毒的个人电脑会随机向外发送大量的ICMP包以及向目的端口为135/137/139/445/1025/5554/9996的端口发送大量的广播包,造成路由器端口拥塞,直至用户整个内部网络/外部网络的瘫痪。
在HiPER上可以用两种方式来检测是否中“震荡波”病毒:
1)通过图形界面的上网监控单击查询命令,如果在外网端口看到大量的445端口,可以判断192.168.0.153这台PC中了“震荡波”病毒
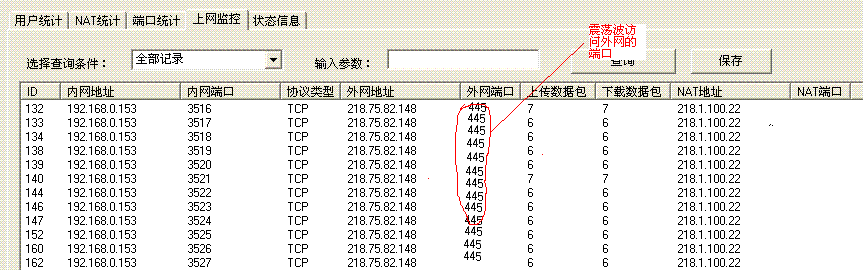

2) 命令行使用show ip nat translation 命令查找感染“震荡波”病毒的个人电脑。
Hiper% show ip nat translation
list all translations
Id srcAddress sPort P destAddress dPort outP inP globalIp
1 192.168.0.153 3516 T 218.7.38.2 445 812 7 218.1.100.22
2 192.168.0.153 3517 T 202.96.209.5 445 346 1 218.1.100.22
3 192.168.0.153 3518 T 218.7.38.2 445 532 7 218.1.100.22
4 192.168.0.153 3519 T 65.54.249.126 445 60 51 218.1.100.22
……………….
可以看出192.168.0.153在向外大量的发送ICMP包已及向目标端口445大量发送数据包,可以判断感染了“震荡波”病毒。
Hiper% show ip nat translation
list all translations
Id srcAddress sPort P destAddress dPort outP inP globalIp
1 192.168.0.153 3516 T 218.7.38.2 445 812 7 218.1.100.22
2 192.168.0.153 3517 T 202.96.209.5 445 346 1 218.1.100.22
3 192.168.0.153 3518 T 218.7.38.2 445 532 7 218.1.100.22
4 192.168.0.153 3519 T 65.54.249.126 445 60 51 218.1.100.22
……………….
可以看出192.168.0.153在向外大量的发送ICMP包已及向目标端口445大量发送数据包,可以判断感染了“震荡波”病毒。
3、在路由器上采用IP Filter的方法,可以屏蔽路由器向外网发送病毒数据包。
命令行模式下:
//关闭TCP 135端口
new filter in/1
set filter in/1 type ip
set filter in/1 forward no
set filter in/1 ip protocol 6
set filter in/1 ip destport 135
set filter in/1 ip destportcmp eql
命令行模式下:
//关闭TCP 135端口
new filter in/1
set filter in/1 type ip
set filter in/1 forward no
set filter in/1 ip protocol 6
set filter in/1 ip destport 135
set filter in/1 ip destportcmp eql
//关闭TCP 137端口
new filter in/2
set filter in/2 type ip
set filter in/2 forward no
set filter in/2 ip protocol 6
set filter in/2 ip destport 137
set filter in/2 ip destportcmp eql
new filter in/2
set filter in/2 type ip
set filter in/2 forward no
set filter in/2 ip protocol 6
set filter in/2 ip destport 137
set filter in/2 ip destportcmp eql
//关闭TCP 139端口
new filter in/3
set filter in/3 type ip
set filter in/3 forward no
set filter in/3 ip protocol 6
set filter in/3 ip destport 139
set filter in/3 ip destportcmp eql
new filter in/3
set filter in/3 type ip
set filter in/3 forward no
set filter in/3 ip protocol 6
set filter in/3 ip destport 139
set filter in/3 ip destportcmp eql
//关闭TCP 445端口
new filter in/4
set filter in/4 type ip
set filter in/4 forward no
set filter in/4 ip protocol 6
set filter in/4 ip destport 445
set filter in/4 ip destportcmp eql
new filter in/4
set filter in/4 type ip
set filter in/4 forward no
set filter in/4 ip protocol 6
set filter in/4 ip destport 445
set filter in/4 ip destportcmp eql
//关闭TCP 1025端口
new filter in/5
set filter in/5 type ip
set filter in/5 forward no
set filter in/5 ip protocol 6
set filter in/5 ip destport 1025
set filter in/5 ip destportcmp eql
new filter in/5
set filter in/5 type ip
set filter in/5 forward no
set filter in/5 ip protocol 6
set filter in/5 ip destport 1025
set filter in/5 ip destportcmp eql
//关闭TCP 5554端口
new filter in/6
set filter in/6 type ip
set filter in/6 forward no
set filter in/6 ip protocol 6
set filter in/6 ip destport 5554
set filter in/6 ip destportcmp eql
new filter in/6
set filter in/6 type ip
set filter in/6 forward no
set filter in/6 ip protocol 6
set filter in/6 ip destport 5554
set filter in/6 ip destportcmp eql
//关闭TCP 9996端口
new filter in/7
set filter in/7 type ip
set filter in/7 forward no
set filter in/7 ip protocol 6
set filter in/7 ip destport 9996
set filter in/7 ip destportcmp eql
new filter in/7
set filter in/7 type ip
set filter in/7 forward no
set filter in/7 ip protocol 6
set filter in/7 ip destport 9996
set filter in/7 ip destportcmp eql
//打开GENERIC层,允许其他类型的数据包
new filter in/10
set filter in/10 type GENERIC
set filter in/10 forward yes
new filter in/10
set filter in/10 type GENERIC
set filter in/10 forward yes
//在e/1上启用filter
set interface ethernet/1 ip filter enable
set interface ethernet/1 ip filter enable
//保存
write
write
关闭以上端口虽然可以使病毒包不影响外网,但是病毒数据量过高仍然会影响到路由器的正常工作。当务之急是找出网络里面工作异常的机器。可以使用路由器show ip mac命令来检查。
Id MacAddress IpAddress IF Age InUcast InNUcast OutPkts
Id MacAddress IpAddress IF Age InUcast InNUcast OutPkts
1 00:03:0f:fb:32:c7 192.168.0.57 0 0:00:00:00 67639 33 78314
2 00:03:0f:fb:3f:cb 192.168.0.36 0 0:00:00:05 2350 25 2520
其中InUcast是单播包的数量,InNUcast是广播包的数量。而正常的机器广播包的数量应该小于单播包的10%。
2 00:03:0f:fb:3f:cb 192.168.0.36 0 0:00:00:05 2350 25 2520
其中InUcast是单播包的数量,InNUcast是广播包的数量。而正常的机器广播包的数量应该小于单播包的10%。











 沪公网安备 31011702003579号
沪公网安备 31011702003579号